Representation on the draft Amendment Directions for exemption from registration to eligible NBFCs
 Loading…
Loading…
 Loading…
Loading…
 Loading…
Loading…
The RBI’s proposed relief to exempt pure investment companies from exemption from regulation is not a cakewalk but a hurdle race. It is not an exemption that comes in auto mode; you need to earn the right to be exempt. Some of the important pre-conditions that the RBI has proposed are:

| Type of NBFC | Options Available |
| NBFCs holding Type I Registration as on April 1, 2026 | Option 1: Apply for deregistration Option 2: Continue to remain as Type I NBFC |
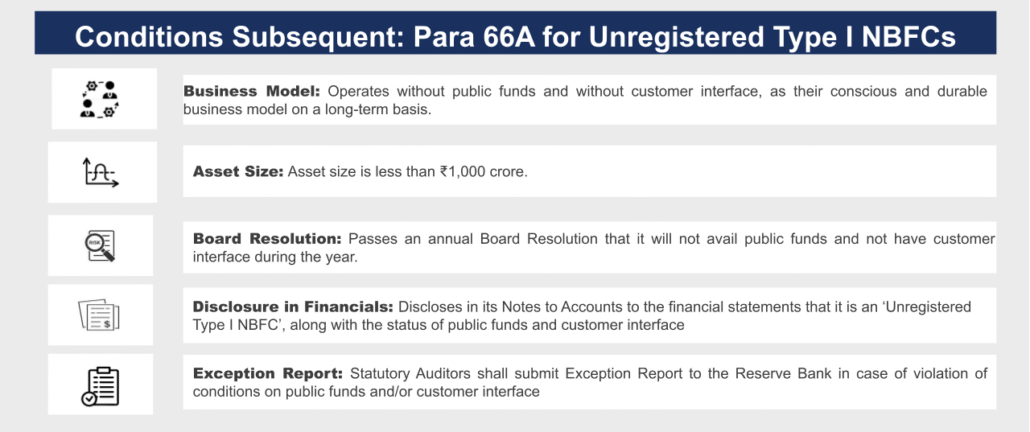
| Entities that fulfil the conditions for Unregistered Type I NBFC, after April 1, 2026 | Option 1: Satisfy the conditions under 66A and remain unregistered [see box on Conditions Subsequent] Option 2: Apply for registration as Type I NBFC |
| NBFCs not having a customer interface and public funds and having an asset size below ₹1000 crores, but not registered as Type I | Option 1: Apply for deregistration Option 2: Apply for registration as Type I NBFC to avail regulatory exemptionOption 3: Maintain status quo |
| NBFCs not having a customer interface and public funds and having asset size above ₹1000 crores, but not registered as Type I | Option 1: Apply for registration as NBFC Type I Option 2: Apply for registration as NBFC Type II, in case of changes in business model |
Several NBFCs that have been registered with the RBI before the concept of Type 1 was introduced in 2016 may not have the CoR as a Type 1 NBFC in spite of the fact that as on date they don’t have access to public funds nor any customer interface. Such an NBFC with an asset size less than ₹1000 crores will still have an option to apply for deregistration, subject to the satisfaction of the conditions prescribed. However, such NBFCs in case they decide to maintain the status quo will not be eligible for the regulatory exemption available to Type 1 NBFCs.
If an entity carries investment activity with owned funds, within a limit of ₹1000 crores, does it need RBI registration? The answer seems to be – no. Such a company obviously does not have to go through the rigour of seeking registration first, and then qualifying for an exemption.
The company in question still has to satisfy the exemption conditions; and the auditor will need to give an exception report. The meaning of exception report is that if there is a breach of any of the conditions of exemption, or there is any breach of any other provisions of the law, the auditor shall be required to make an exception report.
Notably, CARO Order also requires auditors to comment on adherence to RBI regulations, which, in future, will include these conditions too.
Is the requirement of asset size being within ₹1000 crores based on stand-alone financial statements, or will the assets of companies within the group be aggregated, as is done for the purpose of determination of the middle layer status of companies?
It seems that the aggregation requirement is not there for the Type 1 exemption.
The basis for this is FAQ 13, which states as follows:
Q13. As per regulations of the Reserve Bank, total assets of all the NBFCs in a Group are consolidated to determine the classification of NBFCs in the Middle 11 Layer. What shall be the treatment given to ‘Type I NBFCs’ and ‘Unregistered Type I companies’ in this regard?
Ans: For aggregation purposes, the asset size of ‘Type I NBFCs’ shall be considered but asset size of ‘Unregistered Type I NBFCs’ shall not be considered. It is emphasized that ‘Type I NBFCs’ shall always be classified in Base Layer regardless of such aggregation.
Are the exemption conditions, that there is no access to public funds and no customer interface, merely a statement of intent, or must also be borne out by the conduct in any of the past 3 financial years? Looking at the definition in para 6 (14A), which reads “Not accepting public funds and not intending to accept public funds”, and likewise, “Not having customer interface and not intending to have customer interface”, it appears that the exemption conditions are both a statement of fact as well as intent. If one is negated by the fact, a mere statement of intent may not help.
However, assume there are isolated instances of intra-group loans taken or intra-group loans given. The transactions are not indicating a “business model”, at least the ones on the asset side. Are we saying that the breach of the conditions of “no public funds” and “no customer interface”, at any time during the last 3 years, will disentitle the exemption?
We do NOT think so. There are two reasons to say this:
In our view, since the deregistration application has to be made within September 30, 2026, the audited financials for FY 25-26 must have been prepared. Hence, the last three financial years that would be considered are FY 23-24, 24-25 and 25-26.
It is usually hard to get a relief from a regulator, as relief is seen as a prize that you earn. If the idea was based on the premise that what does not matter for the financial system, and is still being regulated, is a burden both for the regulator and for the regulated, there would have been a more welcoming approach to exemption. Specifically:
– Dayita Kanodia, Assistant Manager | finserv@vinodkothari.com
Holding Companies whose primary intent is to invest in their group companies have lately faced a paradox with respect to the requirement of registration as a Core Investment Company (CIC).
CICs are entities whose principal activity is the acquisition and holding of investments in group companies, rather than engaging in external investments or lending exposure outside the group. Para 3 of the Reserve Bank of India (Core Investment Companies) Directions, 2025 (‘CIC Directions’) prescribes the quantitative thresholds for classification of an NBFC as a CIC. In terms thereof, an NBFC that holds not less than 90% of its net assets in the form of investments in group companies, of which at least 60% is in equity instruments, is classified as a CIC and is required to obtain registration from the RBI, unless exempted.
Conceptually, a CIC is a sub-category of a Non-Banking Financial Company (NBFC) (para 3 of the CIC Directions), just like Housing Finance Companies, Micro Finance Institutions, etc. The threshold criteria that NBFCs are required to satisfy is the principal business criteria (PBC), pursuant to which at least 50% of the total assets of the entity must consist of financial assets and at least 50% of its total income must be derived from such financial assets.
The PBC has historically served as the foundational threshold for determining whether an entity is an NBFC. Once the entity satisfies this principal requirement of carrying out financial activity, the sub-category is to be determined based on its line of business, which, lately, has seen quite a varietty – fron tradtional variants such as investment and lending activities (ICC), to housing finance (HFC), to financing of receivables (Factoring companies), the more recent inclusions are account aggregators (AA), mortgage guarantee companies (MGCs), infrastructure finance compaies (IFC), etc. Each of these NBFCs first, and then they fall in their respective class. For instance, HFCs are a type of NBFCs that primarily focus on extending housing loans and hence, must have a minimum housing loan portfolio of 60% and an individual housing loan of 50%.
Accordingly, all categories of NBFCs must first be ascertained to be carrying out financial activities as their primary business, and thereafter, the specific product helps to determine the category. Consequently, holding companies or CICs should ideally also adhere to the 50-50 criteria first and thereafter meet the 90-60 criteria for CIC classification.
However, there is a common perception among the market participants that CICs, irrespective of meeting such PBC, in case they reach the 90-60 criteria, will be required to obtain registration as a CIC. Several news reports also note this perception.
This perception among the market participants that CICs are not required to adhere to the PBC criteria stems from para 17(3) of the CIC Directions, which explicitly provides that:
“CICs need not meet the principal business criteria for NBFCs as specified under paragraph 38 of the Reserve Bank of India (Non-Banking Financial Companies – Registration, Exemptions and Framework for Scale Based Regulation) Directions.”
It may be noted that the above-quoted provision, which has recently been made a part of the CIC Directions pursuant to the November 28 consolidation exercise, was earlier included in the FAQs released by RBI on CICs. FAQs are RBI staff views; whereas Directions or Regulations are a part of subordinate law; however, in the consolidation exercise, a whole lot of FAQs and circulars became a part of the Directions.
Going by the intent of the NBFC classification and categorisation, the above-quoted provisions seem more relevant for registered CICs, implying that CICs once registered need not meet the PBC on an ongoing basis. CICs predominantly hold investments in group companies and therefore satisfy the 90–60 thresholds, but often do not derive any financial income from such investments. Group investments, being strategic in nature, are rarely disposed of, and the dividend income from such investments depends on the dividend/payout ratio, which may be quite low. In several cases, such entities continue to earn income, say, by way of royalty for a group brand name. Even the slightest of non-financial income will seem to breach the PBC criteria, which may challenge the continuation of registration of the CIC as an NBFC. In order to redress this, the provision under para 17(3) of the CIC Directions provides that CICs need not meet the PBC criteria on an ongoing basis.
What is the basis of this argument? The definition of a CIC comes from para 3, which says as follows: “These directions shall be applicable to every Core Investment Company (hereinafter collectively referred to as ‘CICs’ and individually as a ‘CIC’), that is to say, a non-banking financial company carrying on the business of acquisition of shares and securities, and which satisfies the following conditions.” Para 17 (3) is a note to Para 17, which apparently deals with conditions of continued registration.
Given that CIC is a category of NBFC, it would be counter-intuitive to say that the regulatory requirement requires holding companies to go for registration as a CIC even if they do not meet the PBC for an NBFC. In fact, if an entity is not an NBFC because it fails the principality of its business, it would not even come under the statutory ambit of the RBI by virtue of section 45-IC.
Accordingly, without going by just the text of the regulations, in our view, considering the regulatory intent, the following could be inferred:
Other Resources:
 Loading…
Loading…
Our Resources
Simrat Singh | finserv@vinodkothari.com
The Economic Survey 2026 takes an honest view of India’s microfinance sector. Rather than celebrating credit growth alone, it frames microfinance as a household balance-sheet business, where the real test of success is whether borrowing improves stability and resilience at the last mile or not. NBFC-MFIs, as the primary delivery channel, sit at the heart of this assessment. In this short note, we explore major observations of the Survey w.r.t infrastructure financing and microfinance.
The Survey reiterates the importance of microfinance in extending formal credit to underserved households. Women account for the vast majority of borrowers and most lending continues to be rural. Over the past decade, the sector has expanded rapidly in both outreach and scale, with NBFC-MFIs accounting for the largest share of lending, followed by banks and small finance banks.
This expansion has made microfinance one of the most effective channels for last-mile credit delivery but it has also exposed the sector to sharper credit cycles.
The slowdown seen in FY25 is presented as a supply-side correction rather than a failure of the model. The Survey attributes the stress primarily to over-lending and borrower over-indebtedness in certain regions, driven by multiple lenders targeting the same customer base after the pandemic. The key takeaway being that access to credit was not the constraint credit discipline was.
NBFC-MFIs remain indispensable to microfinance, but the Survey recognises their structural vulnerability during rapid growth phases. Unsecured lending and limited visibility into borrowers’ total debt make the model sensitive to concentration risks. Regulatory responses have therefore focused on restoring balance rather than tightening credit indiscriminately. The RBI’s decision to lower the minimum qualifying asset requirement has given NBFC-MFIs room to diversify, while self-regulatory measures have reinforced borrower-level safeguards. The Survey notes early signs of stabilisation in asset quality and disbursement trends.
A recurring concern in the Survey is the lack of reliable tools to assess household income and repayment capacity. Many borrowers carry obligations beyond microfinance such as gold loans or agricultural credit that are not always visible at the point of lending. The Survey sees digital public infrastructure as a gradual solution. Wider use of digital payments, data sharing frameworks and account aggregators is expected to improve cash-flow assessment and reduce reliance on informal income proxies. Using all this information about its borrowers, the MFIs are expected to improve their credit assessment.
One of the Survey’s most important observations is its critique of how success in microfinance is measured. While private capital has helped scale the sector, growth-centric metrics can unintentionally encourage repeated lending without sufficient regard for borrower outcomes. The Survey argues for a shift towards welfare-oriented indicators such as income stability, reduction in distress borrowing and sustainable debt levels rather than portfolio size alone. In doing so, it challenges the assumption that more credit automatically translates into better outcomes.
The Survey neither dismisses microfinance nor romanticises it. It acknowledges its critical role in inclusion, while warning that unchecked expansion can weaken household balance sheets. Long-term sustainability, it suggests, depends less on how fast credit grows and more on how responsibly it is delivered. The Economic Survey’s message is simple: the future of microfinance lies in lending better, not lending more. For NBFC-MFIs, this means aligning growth with borrower capacity, using data more intelligently and treating household stability, not loan volumes, as the true measure of success.
Read our other resources
Climate Finance: domestic resources insufficient to bridge funding gaps
– Team Finserv | finserv@vinodkothari.com
 Loading…
Loading…
– Chirag Agarwal & Siddharth Pandey | finserv@vinodkothari.com
The framework for Integrated Ombudsman Scheme (IOS) constitutes a cornerstone of the RBI’s customer protection and grievance redressal mechanism across the financial sector. With the objective of providing customers a single, unified and accessible platform for redressal of complaints against Regulated Entities, the RBI introduced the Integrated Ombudsman framework.
The RBI has now introduced the Reserve Bank – Integrated Ombudsman Scheme, 2026 (“IOS 2026”), which supersedes the earlier Reserve Bank – Integrated Ombudsman Scheme, 2021 (“IOS 2021”). The new Scheme shall come into force with effect from July 1, 2026.
The IOS 2026 seeks to refine and reinforce the existing mechanism by expanding the scope of coverage, strengthening the powers of the Ombudsman, tightening procedural timelines, enhancing disclosure and reporting. The table below highlights and analyses the key changes introduced under IOS 2026 as compared to the IOS 2021, to enable stakeholders to assess the regulatory and operational impact of the revised framework.
| Provision | IOS 2021 | IOS 2026 | Analysis / Impact |
| Definition of “Customer” & “Deficiency in Service” | The term “Customer” was not defined. Limited definition for ‘Deficiency in Service’, largely linked to users/applicants of financial services. | ‘Customer’ means a person who uses, or is an applicant for, a service provided by a Regulated Entity. (Para 3(1)(h)) ‘Deficiency in Service’ now applicable across all services provided by Regulated Entities and not just restricted to financial services. (Para 3(1)(i)) | Broadens the scope of protection by covering all services offered by Regulated Entities, not just financial services. |
| Definition of “Rejected Complaints” | Not expressly defined | New definition introduced – complaints closed under Clause 16 of the Scheme. (Para 3(1)(o)) | Clarificatory in nature; definition is not used elsewhere in the Scheme |
| Power to Implead Other Regulated Entities | No explicit power | Ombudsman empowered to make other Regulated Entities a party to the complaint if such Regulated Entity has, by an act, negligence, or omission, failed to comply with any directions, instructions, guidelines, or regulations issued by the RBI. (Para 8(6)) | Expands investigative and adjudicatory powers of the RBI Ombudsman |
| Annual Report on Scheme Functioning | The Ombudsman was required to submit an annual report to the Deputy Manager of the RBI; however, the RBI was not obligated to publish it. | It has now been made mandatory for the RBI to publish an annual report on the functioning and activities carried out under the Scheme. (Para 8(7)) | Enhances transparency and public accountability of the Ombudsman framework |
| Interim Advisory | No express provision | Ombudsman expressly empowered, if deemed necessary and based on the circumstances of the complaint, to issue an advisory to the RE at any stage to take such action as may lead to full or partial resolution and settlement of the complaint. (Para 14(6)) | Enables interim reliefs/directions and more effective complaint handling. This would help in resolving disputes by settlement at any stage. IOS permits advisories i.e., communications from the Ombudsman advising REs to take actions for full or partial complaint resolution. Advisories are non-binding and serve as a pre-award tool to facilitate quicker settlements. |
| Principal Nodal Officer (PNO) – Change Reporting | Reporting obligation not specified | Any change in appointment or contact details of PNO must be reported to CEPD, RBI (prior to change or immediately post-change) (Para 18(2)) | Additional intimation requirement for regulated entities |
| Compensation – Consequential Loss | Capped at ₹20 lakh | Enhanced to ₹30 lakh (Para 8(3)) | Increases the limit of potential financial risk for Regulated Entities |
| Compensation – Harassment & Mental Anguish | Consolatory damages capped at ₹1 lakh | Increased to ₹3 lakh (in addition to other compensation) (Para 8(3)) | Compensation limit tripled |
| Limit on Amount in Dispute | No monetary cap | No change – still no limit (Para 8(3)) | Ombudsman continues to have wide jurisdiction irrespective of dispute value |
| Timeline for Filing Complaint | 1 year from RE’s reply; or 1 year + 30 days if no reply from RE | Complaint must be filed within 90 days from the expiry of the RE’s response timeline (30 days) or last communication, whichever is later. (Para 10(1)(g)) | Considerably tightens timelines; this would mean the customers must act swiftly |
| Guidance on Complaint Filing | Dispersed across the Scheme | Consolidated guidance provided in Part A of the Annexure along with Complaint Form. (Annex) | The guidance merely reiterates the points from the scheme that relate to admissibility of a valid complaint, but this is useful for the complainant as he will be aware of the complaint filing requirements and shall not be required to be thorough with the scheme itself |
| Modes of Filing Complaint | Specified the options to file a complaint through portal, email, or courier at CRPC. | Explicitly specified the email-ID of CRPC, and the address at which the complaint shall be couriered. (Para 6(2)) | Specification of the details for filing complaint |
| Data Consent in Complaint Form | No explicit consent requirement | Explicit consent for use of personal data mandatory. (Annex) | Aligns complaint process with evolving data protection and privacy standards |
| Categorisation of Complaints in complaint form | Limited classification | Detailed categorisation of complainant type and nature of complaint. (Annex) | Enables better routing, analytics, and faster resolution |
| Maintainability Check in Complaint Form | No upfront maintainability warning | Explicit note stating non-maintainable scenarios (court pending, advocate filing, etc.). (Annex) | Reduces frivolous filings and early-stage rejections |
| Appellate Authority | Executive Director in charge of concerned RBI department | Executive Director in charge of Consumer Education and Protection Department (CEPD) explicitly designated. (Para 3(1)(a)) | Clarificatory in nature |
| Introduced system-based validation | No such provision | Complaints received via portal, will undergo a system-based validation/check and will be rejected at the outset for being non-maintainable complaints. For the complaints received via e-mail and physical mode, CRPC will assess their maintainability under the Scheme. (Para 12(1)) | This would enhance the “gatekeeping” responsibility of the CRPC, which should speed up the process for valid complaints by weeding out inadmissible ones. |
Other Related Resources:
-Team Finserv | finserv@vinodkothari.com
On January 5, 2026, the RBI issued the Amendment Directions on Lending to Related Parties by Regulated Entities. Pursuant to this, changes were introduced to Reserve Bank of India (Non-Banking Financial Companies – Credit Risk Management) – Amendment Directions, 2026 (CRM Amendment Directions) and Reserve Bank of India (Non-Banking Financial Companies – Financial Statements: Presentation and Disclosures) Directions, Amendment Directions, 2026. Previously, Draft Directions were also issued on the subject. Our write-up on the draft directions can be accessed here.

The amendments under CRM Directions shall apply to all NBFCs, including Housing Finance Companies (HFCs) with regard to lending by an NBFC to its ‘related party’ and any contract or arrangement entered into by an NBFC with a ‘related party’. However, Type 1 NBFCs and Core Investment Companies shall not be covered under the applicability.
These amendments shall come into force on 1 April 2026. NBFCs may, however, choose to implement the amendments in their entirety from an earlier date.
In addition to complying with the provisions of the Amendment Directions, listed NBFCs shall continue to adhere to the applicable requirements of the Securities and Exchange Board of India (Listing Obligations and Disclosure Requirements) Regulations, 2015, as amended from time to time.
Grandfathering of existing arrangements: Existing RPTs that are not compliant with these amendments may continue until their original maturity. However, such loans, contracts, or credit limits shall not be renewed, reviewed, or extended upon expiry, even where the original agreement provides for renewal or review.
Any enhancement of limits sanctioned prior to 1st April 2026 shall be permitted only if they are fully compliant with these amendments.
| RPs under Amendment Directions | Whether covered in the Present Regulations |
| (A) Related Persons: These can be non-corporate | |
| a promoter, or a director, or a KMP of the NBFC or relatives of the said (natural) person | All other persons except the promoter was covered |
| Person holding 5% equity or 5% voting rights, singly or jointly, or relatives of the said (natural) person | No |
| Person having the power to nominate a director through agreement, or relatives of the said (natural) person | No |
| Person exercising control, either singly or jointly, or relatives of the said (natural) person | Yes |
| (B) Related Parties: These can be any person other than individual/HUF, and cover Entities where (A) | Covered Partially |
| is a partner, manager, KMP, director or a promoter | Promoter not covered |
| hold/s 10% of PUSC | Holds lower of (i)10% of PUSC and (ii)₹5 crore in PUSC |
| has single or joint control with another person | Yes |
| controls more than 20% of voting rights | No |
| has power to nominate director on the Board | No |
| are such on the advice direction, or instruction of which the entities are accustomed to act | No |
| is a guarantor/surety | Yes |
| is a trustee or an author or a beneficiary (where entity is a private trust) | No |
| Entities which are related to (A) as subsidiary, parent/holding company, associate or joint venture | Yes |
The definition of “Related Party” remains unchanged from that provided under the Draft Directions.
Further, a clarification have been added where an entity in which a related person has the power to nominate a director solely pursuant to a lending or financing arrangement shall not be regarded as a related party.
Under the Draft directions, the definition of a “related person” included group entities. However, pursuant to the Amendment Directions, group entities have been expressly excluded from the scope of “related person.” The provisions are specific for lending to directors, KMPs and their related parties. In the case of lending to entities such as subsidiaries and associates, the NBFC must adhere to the concentration norms as prescribed under the CRM Directions.
The definition of “Senior Officer” as provided under the erstwhile regulations (Para 4(1)(vii) of the Credit Risk Management Directions) has been omitted and, in its place, the concept of “Specified Employees” has been introduced. “Specified Employees” has been defined to mean all employees of an NBFC who are positioned up to two levels below the Board, along with any other employee specifically designated as such under the NBFC’s internal policy.
Under the erstwhile regulations, the term “Senior Officer” was given the same meaning as defined under Section 178 of the Companies Act, 2013. Thus, the terms Senior Officer included the following:
Practically, this change implies that one additional hierarchical level would now need to be designated as “Specified Employees”. Further, the specific inclusions that earlier applied under the Companies Act and the LODR Regulations i.e., functional heads under the Companies Act and CS and CFO under the LODR will no longer be automatically covered, unless they fall within two levels below the Board or are specifically designated as such under the NBFC’s internal policy.
‘Lending’ in the context of related party transactions would include funded as well as non-fund-based credit facilities to related parties. It may further be noted that investments in debt instruments of related parties are specifically included within the ambit of lending. Accordingly, the scope is not just restricted to loans and advances but includes all fund based and non-fund based exposures as well as investment exposures.
While lending to related parties, the following principles and provisions are to be followed by NBFCs:
The credit policy of the NBFC must contain specific provisions on lending to RPs. Mandatory contents of such policy will include:
Earlier, the policy requirement was specifically applicable in case of base layer NBFCs, but now the same has been made applicable for all NBFCs.
The CRM Amendment Directions also mandate prescribing board-approved limits for lending to RPs. Further, sub-limits will also have to be prescribed for lending to a single RP and a group of RPs. Here, a question may arise on what basis will the NBFC prescribe such limits? Such limits may be prescribed after considering the ticket size of the loans generally offered by the Company, to ensure the loans to RPs are aligned with the loan products for general customers. The limit may be specified as a percentage of the NOF of the NBFC, similar to the credit concentration limits.
NBFCs may extend credit facilities to related parties in accordance with their Board-approved credit policy. Any such lending must be within the board-approved limit prescribed for lending to RPs (including a single RP and a group of RPs).
Further, under the Amendment Directions (Para 13G of the CRM Amendment Directions), RBI has now clearly laid down materiality thresholds for such lending to related parties, including those to directors, senior officers, and their relatives. Lending above the prescribed materiality threshold should be sanctioned by the Board/Board Committee of the NBFC. (other than the Audit Committee).
It may be noted that earlier, for middle and upper layer NBFCs, any loans aggregating to ₹ 5 Crore and above were to be sanctioned by the Board/Board Committee. The materiality thresholds prescribed under the Amendment Directions are based on the layer of the NBFC, as follows:
| Category of NBFCs | Materiality Threshold |
| Upper Layer and Top Layer | ₹10 crore |
| Middle Layer | ₹5 crore |
| Base Layer | ₹1 crore |
| Layer of the NBFC shall be based on the last audited balance sheet.For loans, materiality threshold shall apply at individual transaction level | |
Can the power to sanction loans be delegated to the Audit Committee?
The CRM Amendment Directions have defined the Committee on lending to related parties which will mean a committee of the Board of the NBFC entrusted with sanctioning of loans to related parties. NBFCs may also identify any existing Committee, other than the Audit Committee, for this purpose.
Further, para 13I provides that,
However, a NBFC at its discretion, may delegate the above powers of lending beyond the materiality threshold to a Committee of the Board (hereafter called Committee) other than the Audit Committee of the Board
Accordingly, on a reading of the above, it seems that the power to sanction loans cannot be provided to the Audit Committee of the Board.
5. Quid Pro Quo Arrangements
The CRM amendment directions also provide that any arrangements which aim at circumventing the Amendment Directions will be treated as lending to RPs. Accordingly, any such arrangements involving reciprocal lending to related parties shall be subject to all the provisions of this direction.
Para 13J requires that Directors, KMPs and specified employees must recuse themselves from any deliberations or decision-making on loan proposals, contracts or arrangements that involve themselves or their related parties. This obligation also applies to all subsequent decisions involving material changes to such loans, including one-time settlements, write-offs, waivers, enforcement of security and implementation of resolution plans, to ensure independence and avoid conflicts of interest.
Details of exposure to related parties as per these Directions shall be disclosed in the Notes To Accounts pursuant to para 21(9A) of the Reserve Bank of India (Non-Banking Financial Companies – Financial Statements: Presentation and Disclosures) Directions, 2025 in the following format:
| (Amt in ₹ Crore) | |||
| Sr. No | Particulars | Previous Year | Current Year |
| Loans to Related Parties | |||
| 1 | Aggregate value of loans sanctioned to related parties during the year | ||
| 2 | Aggregate value of outstanding loans to related parties as on 31st March | ||
| 3 | Aggregate value of outstanding loans to related parties as a proportion of total credit exposure as on 31st March | ||
| 4 | Aggregate value of outstanding loans to related parties which are categorized as: | ||
| (i) Special Mention Accounts as on 31st March | |||
| (ii) Non-Performing Assets as on 31st March | |||
| 5 | Amount of provisions held in respect of loans to related parties as on 31st March | ||
| Contracts and Arrangements involving Related Parties | |||
| 6 | Aggregate value of contracts and arrangements awarded to related parties during the year | ||
| 7 | Aggregate value of outstanding contracts and arrangements involving related parties as on 31st March | ||
| Parameters | Existing Guidelines | Amendment Directions |
| Applicability | NBFC-BL- only policy requirement was prescribedNBFC-ML and above – threshold, approval and reporting was applicable | NBFCs in all layers, except Type 1 and CICs |
| Materiality Threshold/ Threshold for seeking board approval | NBFCs-BL- As per the PolicyNBFCs-ML- Rs. 5 croreNBFCs-UL- Rs. 5 crore | NBFCs-BL- Rs. 1 croreNBFCs-ML- Rs. 5 croreNBFCs-UL- Rs. 10 crore. Lending beyond the MT requires board or board committee approval (other than AC). |
| Board approved limits for lending to RPs | No such limit was required to be prescribed | Policy shall specify aggregate limits for loans towards related parties. Within this aggregate limit, there shall be sub-limits for loans to a single relatedparty and a group of related parties.Lending beyond the board approved limit, requires ratification by the Board/AC. |
| Monitoring | Loans and Advances to Directors less than ₹5 crores shall be reported to the Board. Further, all loans and advances to senior officers shall be reported to the Board. | Para 13K: Maintain and periodically update list of related persons, related parties, and loans to them. Para 13L: Annually report credit facilities to specified employees and relatives to the Board. Para 13M: Quarterly or shorter internal audit reviews on adherence to related party guidelines. Para 13N: Report deviations and reasons to the Audit Committee or Board. Para 13O: Products/structures circumventing Directions (reciprocal lending, quid pro quo) shall be treated as related party lending. |
| Policy Requirement | Only for NBFC-BL. NBFCs were required to prescribe a threshold beyond which the loans shall be required to be reported to the Board | Applicable for all NBFCs. |
| Recusal by interested parties | Directors who are directly or indirectly concerned or interested in any proposal should disclose the nature of their interest to the Board when any such proposal is discussed | Interested parties, including specified employees to recuse themselves |
| Disclosure under FS | Related Party Disclosure were specified as per format prescribed under Para 21(9) of Financial Statement Disclosures Directions | In addition to the earlier requirement, another format has been prescribed under Para 21(9A) with respect to details of exposures to related parties |
| Power to sanction loans to RPs | For NBFCs-BL: Only reporting is required; no board approval For NBFCs-ML and above: Board approval required for loans above the threshold. | For all NBFCs:Loans above materiality threshold shall be sanctioned by Board or delegated Committee (not Audit Committee) Loans below the threshold shall be sanctioned by appropriate authority as defined under the Policy. |
Our Other Resources:
-Archisman Bhattacharjee | finserv@vinodkothari.com
The Digital Personal Data Protection Act, 2023 (“DPDPA”), along with the Digital Personal Data Protection Rules, 2025 (“DPDP Rules’, “Rules”), establishes India’s first comprehensive and rights-based data protection regime. The Act’s applicability extends far beyond financial institutions; it encompasses any entity, large or small, digital or traditional, that processes digital personal data. Although public discourse frequently associates data protection obligations with banks, fintech companies, and large technology entities, the DPDPA’s scope is intentionally crafted to be broad and sector-agnostic. As a result, non-financial entities operating in fields such as FMCG, real estate, healthcare, hospitality, education, retail, and even small kirana shops using basic digital systems are brought squarely within its regulatory ambit.
This wide applicability stems from the Act’s fundamental design. It regulates processing, not industry classification. As long as an entity processes any digital personal data, whether it is a customer’s name and phone number, an employee’s email address, a patient’s medical record, or a tenant’s identity document, the DPDPA applies, unless a statutory exemption is granted.
This article examines the applicability of the DPDPA to non-financial entities, analyses the lawful bases for processing personal data, evaluates sector-specific implications, discusses whether corporate data is included within the scope of “personal data”, and explores the operational and regulatory obligations, including security safeguards, deletion timelines, and Data Principal rights. A supporting analysis of Section 17 of the DPDPA which empowers the Central Government to exempt certain entities is also provided, along with the practical question of whether small businesses such as kirana stores may eventually be exempted.
The applicability of the DPDPA flows from Section 3, which states that the Act applies to the processing of digital personal data (including personal data which is collected physically and digitised later) within the territory of India and to processing outside India if the processing is connected with any activity of offering goods or services to data principals within the territory of India. There is no carve-out or exception based on the nature of the business, regulatory environment, or industry classification of the entity. Consequently, companies operating in sectors such as fast-moving consumer goods (FMCG), real estate, hospitality, e-commerce, education, healthcare, and professional services must comply with the Act if they process digital personal data.
The definition of “personal data” under Section 2(t) is intentionally broad, referring to any data about an identified or identifiable individual. This broad definitional standard ensures that even the most basic identifiers such as, names, phone numbers, email addresses, login credentials, and customer records fall within the purview of the Act. As a result, non-financial entities that process personal information of customers, employees, patients, visitors, students, tenants, or vendors automatically become “data fiduciaries” under Section 2(i) and must meet all obligations imposed by the Act.
The core philosophy underlying the DPDPA is processing-centric regulation. The Act deliberately avoids distinguishing entities based on their business sector, risk level, or regulatory regime. Instead, it focuses on the fundamental principle that any organisation handling personal data plays a significant role in the digital ecosystem. Non-financial entities have dramatically increased collection and utilisation of personal data for purposes such as digital marketing, analytics, supply-chain management, customer engagement, employee administration, and third-party platform integrations. This reality makes them equally capable of causing privacy harms or security breaches as financial institutions, and hence equally subject to regulation.
Moreover, non-financial sectors operate extensive digital infrastructure, such as e-commerce platforms, CRMs, ERPs, AI-based analytics systems, CCTV surveillance networks, and biometric verification systems, that rely heavily on personal data. These systems are vulnerable to cyberattacks, unauthorised access, data misuse, profiling, and identity theft. By bringing them fully within the regulatory framework, the DPDPA ensures a uniform accountability standard across the Indian digital economy.
Small business owners including kirana shops, local merchants, fitness coaches, small doctor’s clinics, tuition centres, neighbourhood restaurants and small real-estate brokers frequently engage in personal data processing such as storing customer phone numbers for order delivery, maintaining digital records for loyalty schemes, providing receipts digitally etc. The Act, as it stands, does not grant automatic exemptions for such entities. They are expected to issue notices, collect valid consent where applicable, respect withdrawal, ensure reasonable security safeguards, and delete data once the purpose is achieved.
This creates a compliance burden that many micro-enterprises lack the resources to fulfil. The proportionality concerns are evident: penalties under the Act may reach hundreds of crores, even though government statements indicate that penalties will be imposed only where there is significant negligence or wilful misconduct.
The presence of Section 17(3), however, signals clear legislative recognition that small entities may require differentiated treatment. It remains reasonably likely that the government may, in future, exempt certain classes of micro-entities processing minimal personal data from certain provisions of the Act as provided under Section 17(3) and declare them as “low-risk data fiduciaries” with reduced compliance requirements.
Such exemptions would be consistent with global practice: for instance, GDPR permits reduced compliance obligations for small data volumes and uses a risk-based approach. Until notifications are issued, however, all entities including small merchants who are processing digital personal data, remain subject to the Act.
Under the DPDPA, the only lawful basis for processing personal data without consent is the limited set of “legitimate uses” specified under Section 7. Unlike earlier drafts of the Bill or international frameworks like the GDPR, “contractual necessity” or “contractual obligation” is not included as a legitimate use under the enacted DPDPA. This is a deliberate departure from global practice and means that entities cannot rely merely on contractual engagement to justify processing of personal data without consent.
Consent therefore becomes the primary lawful basis for most private-sector organisations, especially in non-financial sectors. Consent must meet the requirements of Section 6 and must be preceded by a detailed notice under Section 5. Withdrawal of consent must be as easy as its grant, placing significant obligations on data fiduciaries.
Legitimate uses under Section 7 remain narrow and apply primarily to scenarios such as compliance with law or judicial orders, medical emergencies, safeguarding individuals during disasters, and other notified public-interest functions. Most routine commercial operations in FMCG, real estate, healthcare, retail, and education do not fall within legitimate use and therefore require consent-based processing.
FMCG companies, both digital-first and traditional, routinely collect and process large volumes of personal data, often through online portals, mobile applications, loyalty cards, e-commerce platforms, and promotional events. Customer names, phone numbers, addresses, behavioural data, purchase histories, and feedback form the core of their data-driven marketing strategy. Because “contractual necessity” is not a legitimate use under the DPDPA, almost all customer-facing processing requires consent, particularly marketing, profiling, analytics, and preference tracking
Additionally, FMCG entities store substantial employee personal data, which may be processed under legitimate uses for employment However, indefinite retention of customer data after fulfilment of the purpose is expressly prohibited under Section 9, mandating regular deletion or anonymisation.
FMCG entities must ensure:
The real estate sector handles sensitive personal data of prospective buyers, tenants, investors, and visitors, including identification documents, financial details, contact numbers, and biometric or CCTV data for access control in residential and commercial complexes. Most of this data is collected for contractual and compliance purposes under RERA, municipal laws, or verification procedures, placing it within the scope of legitimate uses. Yet, marketing of new projects, cold calling, and database sharing with brokers or partners require explicit consent.
A major compliance challenge in this sector is data retention, since developers often maintain personal records of customers long after project completion or sale. Section 9 makes it clear that data fiduciaries cannot retain personal data beyond the period necessary to satisfy the purpose for which it was collected, unless mandated by law. Real estate entities must therefore implement strict retention schedules and erasure policies.
Given that contractual obligation is not a legitimate use, real estate entities must:
Limited circumstances, such as government-required land/property registration processes, may fall under legitimate use.
Healthcare providers including hospitals, clinics, diagnostic centres, telemedicine platforms, and wellness service providers process exceptionally sensitive categories of personal data, such as health records, medical histories, prescriptions, laboratory results, insurance information, and emergency contact details. While the DPDPA does not create a separate class of sensitive personal data (unlike GDPR’s Article 9), it indirectly imposes a heightened duty of care through Section 8, which mandates reasonable security safeguards for all personal data.
Most healthcare processing is covered under legitimate uses, particularly when it is necessary to provide medical treatment, respond to emergencies, or ensure patient safety. However, collecting personal data for promotional communication, wellness packages, and non-essential data analytics require explicit consent. Healthcare entities must also be mindful of strict deletion timelines under Section 9, ensuring that data is retained only for statutory medical record retention periods and not beyond.
Medical entities must:
A wide range of other sectors also fall fully under the Act’s scope. The hospitality industry collects personal data for guest registration, reservations, and government-mandated identity verification, and must ensure consent for digital marketing, loyalty schemes, or data sharing with travel partners. The e-commerce sector relies heavily on personal data for order fulfilment, logistics, and grievance redressal, but requires explicit consent for recommendation engines and personalised advertising. Educational institutions process student data for academic administration and compliance, requiring parental consent for processing of minors’ data under the DPDP Rules. Manufacturing and industrial entities may process limited personal data, but employee data, vendor contact details, CCTV surveillance footage, and visitor logs still bring them under the scope of the Act.
Processing of employee and vendor personal data requires a nuanced understanding under the DPDPA, because the lawful bases and practical compliance mechanisms differ significantly for each category. In the case of employees, section 7(i) of the Act expressly recognises employment-related purposes as a legitimate use, thereby permitting employers to process the personal data of their employees including candidates, full-time staff, contractors, interns and potential employees without requiring explicit consent, so long as such processing is necessary for recruitment, attendance management, payroll, statutory compliance, or performance evaluation. However, any processing that goes beyond what is necessary for employment for instance, wellness programmes, optional benefits, behavioural analytics, or promotional features must still be based on consent.
However, in contrast, vendor employee related personnel data (names, email IDs, mobile numbers of points of contact) does not fall within any legitimate use category, and contractual necessity is not recognised as a lawful ground under the DPDPA. This leads to a practical challenge: vendors must supply personal data of their representatives for coordination and performance of commercial contracts, yet obtaining individual notices and explicit consent from each representative is often impracticable, and mere inclusion of consent language in the vendor contract does not satisfy the statutory requirement of explicit, informed consent.
To mitigate this, businesses can adopt a multi-layer compliance model. First, during vendor onboarding, companies can require the vendor entity to nominate authorised representatives, and mandate that the vendor obtain explicit consent from those individuals before sharing their information. The obligation can be placed contractually on the vendor to:
While the DPDPA requires explicit consent from the Data Principal, it does not prohibit consent being obtained through an authorised intermediary, provided the intermediary can demonstrate that the individual has indeed given such consent. Second, companies may maintain a publicly accessible privacy notice (e.g., on their website) that applies to all external stakeholders including vendor personnel setting out the purposes of processing, retention periods, rights, and grievance redressal mechanisms. Though a notice must still be “made available,” a standardised publicly available notice reduces the administrative burden of issuing individualised notices in every instance. Third, when communication is initiated with a vendor’s representative for the first time, companies should send a brief digital notice, via email or SMS, giving the individual access to the privacy notice and explaining that their data has been provided by their employer for coordination of contractual activities. This satisfies the obligation of informing the Data Principal even if consent was collected upstream by the vendor. Finally, systems must allow vendor personnel to request correction or deletion of their details, and a replacement representative can be nominated by the vendor entity, enabling ongoing compliance without business disruption.
The DPDPA’s definition of personal data applies strictly to natural persons, and therefore corporate data that does not identify an individual lies outside its scope. However, the boundary can be complex. Email addresses such as firstname.lastname@company.com or name@gmail.com clearly identify specific individuals and therefore may fall within the definition of personal data. Similarly, phone numbers, employee codes linked to individuals, or vendor representative names constitute personal data.
Conversely, generic email addresses such as info@company.com, support@business.com, or legal@gmail.com cannot be traced to a specific individual and therefore would not be considered personal data. This interpretation aligns closely with GDPR Recital 26, which clarifies that data relating to legal persons or generic organisational identifiers does not constitute personal data unless it directly identifies a natural person. Non-financial entities must thus carefully classify their corporate data based on identifiability to avoid over- or under-compliance.
All non-financial entities qualifying as data fiduciaries must comply with Section 8’s mandate to implement reasonable security safeguards, including organisational policies, encryption standards, access controls, periodic audits, vulnerability assessments, and incident response mechanisms. Data breaches must be reported both to the Data Protection Board and to affected data principals in accordance with the DPDP Rules, 2025. Larger non-financial entities may be designated as Significant Data Fiduciaries under Section 10, requiring them to appoint Data Protection Officers, conduct Data Protection Impact Assessments, and undergo independent data audits.
Data principals are granted a suite of rights under Sections 11 to 15, including the right to access information about processing, seek correction or erasure of personal data, nominate a representative for emergency situations, and obtain a grievance resolution in a timely manner. These rights create substantial operational obligations for non-financial entities, which must set up dedicated channels and workflows to address such requests.
Retention and deletion are governed explicitly by Section 9, which requires that personal data be erased once the purpose has been fulfilled and no legal obligation justifies continued retention. This provision significantly impacts sectors that historically maintained extensive archives of customer and employee data with no defined deletion timeline. The DPDP Rules, 2025, require periodic data retention assessments and impose specific timelines for erasure following the withdrawal of consent or completion of purpose.
The DPDPA represents a transformative shift by imposing uniform obligations across all entities that process digital personal data, regardless of the industry in which they operate. Non-financial entities often overlooked in discussions of data protection engage in extensive personal data processing through their digital platforms, operational systems, and customer engagement mechanisms. As a result, they are equally bound by statutory requirements governing lawful processing, consent mechanisms, legitimate uses, security safeguards, erasure obligations, and individual rights. The DPDP Rules, 2025, further operationalise these requirements, placing significant compliance responsibilities on non-financial sectors that must now adopt structured governance frameworks, update internal policies, and strengthen technical safeguards.
As India moves closer to an integrated digital economy, the DPDPA’s application to non-financial sectors ensures that privacy protection becomes a universal standard rather than a sector-specific obligation, aligning the country’s data governance landscape more closely with global frameworks such as the GDPR, while addressing local needs through its own unique regulatory philosophy.
As Justice D.Y. Chandrachud observed in the landmark judgment of K.S. Puttaswamy v. Union of India:
“In the digital economy, every entity that touches personal data becomes a gatekeeper of privacy.”
This statement has become a defining reality in today’s data-driven landscape.
Our other related resources:
