WPR Login
/byLogin
WPR Login
/by Vinod Kothari ConsultantsLogin
WPR Register
/byReporting of Fraud – Resource Centre
/0 Comments/in Uncategorized /by Vinod Kothari ConsultantsWe, here at Vinod Kothari and Company, have curated all our materials and FAQs relating to fraud monitoring and reporting under Companies Act, 2013, SEBI Regulations and RBI Regulations to provide a single point access to our various resources. This page is intended to be a one stop solution to all your queries regarding the same. Hope that the readers find it useful.
देख मत मुड़कर परिन्दे
/0 Comments/in Uncategorized /by Vinod Kothariदेख मत मुड़कर परिन्दे
सामने आकाश का विस्तार है
लोग मापेंगे तुम्हारे फासले जो तय किये हैं
हाथ में फीता लिए
किन्तु तुमको फासलों की है नहीं परवाह
क्षितिज तक उड़ना तुम्हारी चाह
सांस सीने में परों में शक्ति है
अनवरत उड़ना तुम्हारी नियति है, संसार है
देख मत मुड़कर परिन्दे
सामने आकाश का विस्तार है
Profile of Speaker | 11th Securitisation Summit, 2023
/0 Comments/in Uncategorized /by Vinod Kothari ConsultantsSummit home page – https://vinodkothari.com/secsummit/
 Loading…
Loading…
A poem on the problem of climate change, environment and clean energy
/0 Comments/in Uncategorized /by Vinod Kothariकिसी पेड़ ने उस पंछी को अब तक नहीं उड़ाया है
जिसने शाखें नहीं उजाड़ी केवल फल को खाया है
चिड़ी चोंच भर ले जाती है नदी नीर क्या कम होता?
प्यास बुझाकर प्यासे की कब कम होता जल का सोता
शिशु को दूध पिला कर किस माता की घटती काया है?
जब तक सीमाकरण न होगा पर्यावरण बचेगा क्या?
कोटि दुयोधन हाथ, द्रौपदी का आभरण बचेगा क्या?
मोह सँवरण नहीं, प्रकृति का कल्पवृक्ष बच पाया है ?
अगर प्रश्न है जठर अग्नि का जल के कितने स्रोत रखे
कोई ऐसा पेय नहीं जो काम अग्नि को बुझा सके
संयति के दृढ़ तीर न होंगे कब सागर रुक पाया है ?
प्रश्न यह नहीं इस वाहन को कैसी शक्ति चलायेगी
जब तक गति पर रोक न होगी बात वहीं रह जाएगी
सुविधा के गमले में कब शिव का बरगद उग पाया है
Impact of Artificial Intelligence in the Lending Ecosystem
/0 Comments/in Uncategorized /by Staff-Dayita Kanodia, Executive | finserv@vinodkothari.com
“It is the quality of lending over the quantity of lending”
-Lewis Thompson Preston
Banking everywhere but never at a bank[1]
Disbursement in the Indian lending market witnessed a growth of 11 percent and reached Rs.174 trillion in FY22, compared to Rs.11.4 trillion in FY17, with a record growth of CAGR 72 percent. The disbursement is further expected to grow and reach Rs.274 trillion by FY26.
Out of the total lending volumes, India’s digital lending market was worth USD 270 billion in 2022 and is expected to reach USD 350 billion by 2023.[2]
Amid surging demand for online loans, lending institutions are claiming that they are adding more than 10000 users a day and have amassed more than 6 million users to date. It seems that the financial sector has finally accepted the change for ‘banking everywhere but never at a bank’. Given the significance and relevance of this subject, this article intends to discuss how AI is impacting the lending business.
Before delving into the intricacies of artificial intelligence and its use, it is important to note that the financial sector regulator, the Reserve Bank of India, concerned on this mushrooming of digital lending apps, has already come out with various guidelines on digital lending to protect customers’ data and reduce the increasing number of frauds in the system[3]. These regulations by the RBI among other things emphasizes on permitting only regulated entities like banks and non-banking financial institutions to extend loans over a digital platform, provide a mandatory cooling off period and make it compulsory to have a customer’s consent before increasing their credit limit.[4]
Transformation in the lending industry
It is believed that Robotic Process Automation, machine learning and artificial intelligence can together act a set of support mechanisms for internal staff and customers.
The lending process involves a series of activities that lead to the approval or rejection of a loan application. A well- integrated AI, Automation and ML models would enhance the entire lending process, increase it’s efficiency, conjunction with other technologies like OCR and NLP. The majority of documentation work happens during the initial stages of loan processing which are highly time consuming. Enabling automation throughout the lending cycle, AI in loan processing reduces the overall time spent significantly. It can complete much of the credit evaluation and background research faster and without any human intervention.
Loan Monitoring
Companies can easily use Machine Learning to pick out loans that have the possibility to go bad and help to analyze on-going loans. This will help lenders take precautionary steps against borrowers whose loans are likely to default. Again, institutions can combine the AI to automate their debt collection team’s intelligence methods such as AI can spot trends for defaulting loans and refine early response processes, including more detailed and personalized approaches to customers.
Credit-Scoring Scheme
Artificial intelligence can identify risk profiles and assess the ability to pay based on factors other than just the credit score. Again, most of the online transactions are done through a smartphone today, lenders can easily track a prospective customer’s online activity. Therefore, artificial intelligence can build a credit score for them by analyzing their online activities.
Further, AI powered lending tools can scrutinize all the data in the documents and then compare it with the loan requirements and provide meaningful insights that can help the lender make more effective decision on the borrower’s creditworthiness.
Artificial Intelligence and Machine Learning can allow lenders to look beyond credit scores and see data patterns that can help establish the character and capability to repay -that are the foundation of lending. For instance, inexperienced or new borrowers do not have a credit history and therefore their credit scores do not necessarily reflect their likelihood of repaying a loan, but their complete tradeline data can offer more detail about the timeliness of their payments and other behaviors that may qualify them for certain lending products.
Artificial Intelligence and Machine Learning can help banks and lending organizations improve rule based underwriting. These advancements have a major impact on accuracy, particularly while processing loan applications in bulk.
Meeting Customer Expectations
A seamless client onboarding process is the first step in making a great first impression. It all starts with a potential lead which connects with the sales team and goes through several steps to compile crucial data and carry out the various regulatory, legal and due diligence checks.
At present, a large part of the commercial banking system are based on human networking. The dependence on human intervention not only impacts speed but also results. AI has removed this by churning the applications through its algorithms to search for patterns and deliver insights and decisions based on the same. Therefore, zero emotions are involved.
ChatBots have grounded itself as a strong tool for customer satisfaction and is thus an unmatched support for the organisations supporting them to save a lot of time and cash. AL and ML have ensured that there is less chance for errors and provides organisations with exceptional analytical and clear thinking.
Automating the complicated lending process and streamlining it to provide results in a matter of minutes by using AI and ML is a win for the lending industry as the faster the lenders churn loans, the better their revenues and profit margins, and the happier the customers.
We can say that customer delight has become a fact rather than a myth in the age of AI and ML in lending.
Can AI do everything?
We cannot ignore the fact that relationship banking plays a large part in the entire lending- borrowing process. Companies do not necessarily take loans from the bank which offers them the cheapest finance. Instead, companies take loans from banks that they consider to be a business partner and have good working relationships with.
One should also consider the fact that artificial intelligence based system is made out of deep neutral networks which take data from a wide variety of sources. The sources of their data as well as the process undertaken to arrive at a decision can be quite complex and may not be completely transparent to a layman.
Hence, the end result is that some of the decisions made by the system are incomprehensible to humans. For instance, the systems may deny a loan to a long time customer of a commercial bank and the reasons may not be easy to decipher.
Concluding remarks
There is requirement for supervised AI which sorts data based on the rules created by humans. This will enable the organizations to be able to deliver even better services by bringing together the best of humans and machine capabilities into their craft, making an even more attractive prospect for their clients. At the end of the day, it is humbling to know that no matter how advanced our technology becomes it cannot replace human creativity, intuition and experience.
[1] Book by Brett King
[2] https://bfsi.economictimes.indiatimes.com/news/fintech/indias-digital-lending-market-worth-270-bln-in-2022-disbursement-grew-by-11-reports/97388937
[3] Our variousother articles on Digital Lending can be read here- https://vinodkothari.com/?s=digital+lending
[4] https://www.rbi.org.in/scripts/NotificationUser.aspx?Id=12382&Mode=0
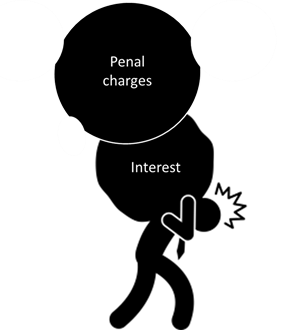
Penal charges not a cash-cow for lenders
/1 Comment/in Financial Services, RBI, Uncategorized /by Vinod Kothari ConsultantsRBI issues draft guidelines on fair lending practices for penal charges
– Aanchal Kaur Nagpal, Manager and Dayita Kanodia, Executive | finserv@vinodkothari.com
Introduction
Levying of penal interest/ charges is a punitive measure adopted by lenders on borrowers defaulting in making repayments and/ or breaching any terms and conditions mutually agreed in the loan agreement. The Reserve Bank of India also allows lenders to charge such rates as long as the same are communicated to the borrower and are in accordance with the Board approved policy framed in this behalf.
However, lenders, cashing in on such autonomy and flexibility, have adopted varied practices which are often prejudicial to the borrower. These include charging exorbitant rates, capitalisation of penal charges, charging of penal interest on the loan amount and not the defaulted portion etc.
The RBI, in its Statement on Developmental and Regulatory Policies dated February 08, 2023[1], announced policy measures for introduction of guidelines for regulating the penal charges levied by financial institutions[2]. Pursuant to the same, RBI, on April 12, 2023 has issued a draft circular on Fair Lending Practice – Penal Charges in Loan Accounts (‘Draft Circular’) to persuade lenders to use penal charges for their true compensatory nature and not as a revenue enhancement tool.
While the Draft Circular comes with good intentions, there are certain provisions that may seem ambiguous and contradictory, and the final guidelines would need to provide sufficient clarity to achieve the desired execution.
Read more →